What is Port 56744 TCP 2024: An In-Depth Guide
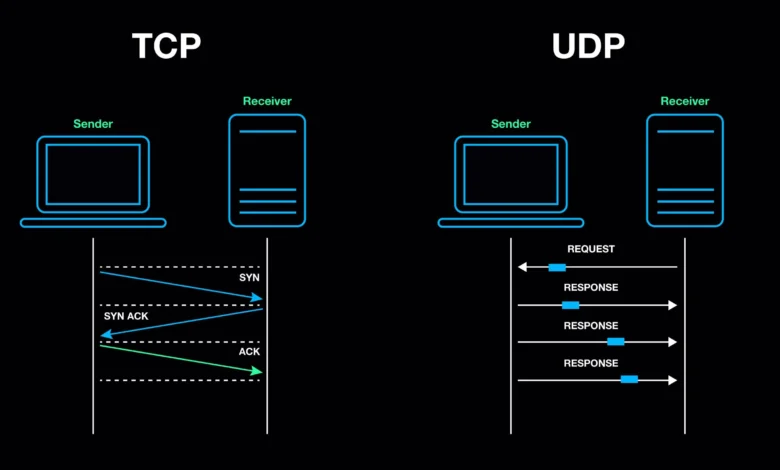
1. Introduction to TCP Ports
What is Port 56744 TCP 2024, TCP (Transmission Control Protocol) ports play a vital role in computer networking by serving as endpoints for communication between devices over the internet or other networks. Each port number identifies a specific process or service running on a device.
The Orthodox Icon Projecting Lie
The Ultimate Guide to the IVACare Stiff Coffee Cup
What is a TCP Port?
A TCP port is a communication endpoint. When data travels across a network using TCP, it is assigned a port number to facilitate routing.
Importance of Ports in Networking
Ports enable devices to send and receive data through the correct channel, ensuring efficient and secure communication.
2. Overview of Port 56744 TCP
Basics of Port 56744
Port 56744 is a high-numbered port, typically used for dynamic or private purposes. High-numbered ports range from 49152 to 65535 and are often used temporarily during network operations.
Common Uses and Associations
While ports such as 80 (HTTP) and 443 (HTTPS) have well-known uses, Port 56744 may not have a standardized or universal application. Its usage can vary based on the needs of different applications and environments.
3. How TCP Ports Work
TCP/IP Protocol and Ports
The TCP/IP protocol suite uses ports to differentiate services and ensure data packets reach their intended application. TCP’s connection-oriented nature requires ports to manage and maintain reliable data transfers.
How Connections are Established
When a client initiates communication with a server, it sends data packets to a destination port. The server, listening on that port, processes the request and sends a response.
4. Purpose of Port 56744 in 2024
Specific Applications in 2024
In 2024, Port 56744 may be used in emerging software solutions, network services, or custom applications that need non-standard ports for dynamic communication.
Changes or Trends in Usage
The increasing need for dynamic port allocation due to the rise in cloud services and complex network structures is shaping the usage of such high-numbered ports.
5. Security Implications of Port 56744 TCP
Potential Vulnerabilities
Like any TCP port, Port 56744 could be exploited by malicious actors for unauthorized access, Denial-of-Service (DoS) attacks, or malware distribution if left unprotected.
Mitigation Strategies
Securing this port involves firewall rules, network monitoring, and regular system updates to guard against vulnerabilities.
6. Configuration and Use Cases
Port Forwarding
Port forwarding allows specific traffic on Port 56744 to be directed to a designated machine or service, useful for scenarios requiring external access.
Use in Firewalls
Properly configuring firewalls to allow or block traffic on Port 56744 can enhance security and control over data flows.
7. Typical Scenarios Where Port 56744 is Used
Communication Protocols
This port may be dynamically allocated for peer-to-peer communications, high-load server responses, or custom data transfer protocols.
Specific Software or Services
Certain network management software or real-time services may utilize Port 56744 for proprietary communication.
8. Monitoring and Managing Port 56744
Network Monitoring Tools
Using tools like Wireshark, Netstat, or Nmap, network administrators can monitor traffic on Port 56744, detect anomalies, and troubleshoot issues.
Troubleshooting Issues
Common challenges include packet losses, connection refusals, or incorrect routing. Correctly diagnosing these requires deep insight into port behavior and network configurations.
9. Common Problems with Port 56744
Connection Refusals
Connection issues on Port 56744 may result from firewall restrictions, incorrect configurations, or server overload.
Data Packet Drops
Dropped packets could indicate network congestion or security measures like rate limiting on this port.
10. How to Open or Close Port 56744
Operating System-Specific Steps
Opening or closing Port 56744 varies by OS. On Windows, for example, you can configure it using the Windows Defender Firewall with Advanced Security tool.
Best Practices
Follow best practices such as testing port rules in non-production environments and enabling logging for monitoring purposes.
11. Firewalls and Port 56744
Role of Firewalls in Port Security
Firewalls act as gatekeepers, controlling incoming and outgoing traffic on Port 56744 and other network ports to ensure security.
Configuring Rules for Port 56744
Creating rules for Port 56744 includes specifying allowed IP addresses, protocols, and connection types.
12. The Role of ISPs and Port 56744
ISP Restrictions and Policies
Some ISPs may restrict certain ports, including Port 56744, to mitigate security risks or manage network usage.
Troubleshooting Connectivity Issues
Work with your ISP to diagnose any access problems related to Port 56744 and determine if restrictions apply.
13. Real-Life Examples of Port 56744 Usage
Case Studies
A real-world use case might involve a software solution utilizing this port for real-time communication between distributed services.
Real-World Benefits
Incorporating Port 56744 can enhance data throughput and enable more customized, flexible networking setups.
14. Risks and Threats Associated with Port 56744
DDoS Attacks
Ports left open without security measures, like Port 56744, can be exploited for Distributed Denial-of-Service (DDoS) attacks.
Malware Exploits
Malware can leverage open or misconfigured ports to infiltrate systems. Regular patching and monitoring help mitigate such risks.
15. Future Outlook for Port 56744
Emerging Technologies Impact
Technologies like edge computing and advanced IoT solutions could influence how high-numbered ports, such as Port 56744, are used.
Evolution of Networking Trends
As network demands increase, ports like 56744 may see expanded use for specialized applications, demanding continuous adaptation in security and management practices.
Frequently Asked Questions (FAQs)
1. What is Port 56744 used for?
Answer: Port 56744 is often used for temporary or private communications in various network applications, depending on configuration needs.
2. How can I secure Port 56744 on my network?
Answer: Use firewall rules, access controls, and network monitoring tools to ensure that only trusted devices and traffic can access Port 56744.
3. Are there any security risks with leaving Port 56744 open?
Answer: Leaving it open without proper security measures can expose the network to risks like DDoS attacks or unauthorized access.
4. Can Port 56744 be blocked by my ISP?
Answer: Yes, some ISPs may block high-numbered ports like 56744 as part of their network management or security policies.
5. How do I check if Port 56744 is open?
Answer: Use network scanning tools like Netstat, Nmap, or Windows Powershell commands to check the port’s status on your system.